 Risk and Audit – A Glimpse
Risk and Audit – A Glimpse
Every organization in pursuit of its Objectives encounters Risks & Perils that hamper growth & sustainability, which have to be contained to meet desired goals. Business, Technological, Operational & Other Risks are its components .Risk management, thus, is as important as the core operations.
Risks ultimately impact the True & Fair presentation of financial data (it being the point of concurrence for all events & operations), in an adverse manner. Auditors, as watchdogs, through their attempts to provide the stakeholders with a reasonable assurance, have now evolved as indispensable and powerful Statutory External tools to check, report & mitigate these adversaries in the form & style of Risk Based Auditing.
Risk Based Auditing (RBA) is designed to efficiently and effectively focus the Nature, Timing and Extent of Audit Procedures to those areas that have the most potential for causing Material Misstatements in the Financial Reports and Management Assertions.
The name is self explanatory – Risks facing an entity form the cornerstone of Audit throughout.
Here, the auditor’s objective is to obtain reasonable assurance that no material misstatements, caused by fraud / error exist at the financial statements and assertion levels. The key components are as follows:
a) Identification & Detection of Risks
b) Assessment & Classification as
1. Significant Risks – requiring special audit considerations.
2. Normal Risks
c) Designing & Implementing Further Audit Procedures (FAP) to Respond to the assessed risks.
d) Issuing Appropriate Audit Report in a manner to reduce the Audit Risk to an acceptably low level.
The Risk based approach entails the auditor to first Understand the Entity and its Environment, including Internal Controls.
Relevant Accounting Standards
SA 315 :- Identifying and Assessing the Risk of Material Misstatements through Understanding the Entity and its Environment – which guides the identification & assessment.
SA 330 :- The Auditor’s Response to Assessed Risks – elucidates the responses
Conventional Approach – Brief View
The auditor generally obtains the understanding of the relevant industry, legal frameworks, operations of entity, governance structure, financing modes, selection & application of accounting policies & strategies to acquaint him with the entity.
The basic knowledge then allows the auditor to identify the loopholes / vulnerable areas through his own observations, inspections of process execution, walkthrough activities, Inquiries with management & staff, external clarifications, past audit reports etc
Analytical Procedures are then employed to assess the significance, relevance of risks to financial reporting and also the likelihood of their occurrence. The control activities relevant to financial reporting are also studied for obtaining sufficient & appropriate audit evidence.
The Responses are then decided & implemented by performing Substantive Procedures – Tests of Details & Substantive Analytical Procedures and also Test of Controls. Requirement of Further Audit Procedures is also considered before issuance of Audit Report to mitigate the Audit Risk.
Transition to Informational Technology Information Systems
No Activity is Immune to Technological changes; Business and Audit are No Exceptions.
Traditional methodology of audits had an audit trail which assisted the auditors in conducting and documenting the audit. However, Auditing in a computerized environment depends on the specific scope & objective. The auditor has to look at both manual and automated parts of the system due to their interfacing nature.
Higher the Technology, Greater is the need for controls. Technology risks are driven by dynamic nature of IT that keeps changing frequently. Auditors, now are required to focus on the entity level response to changes in critical systems that cannot afford to fail.
Auditors may choose either,
Auditing Around the Computer – The Black Box Approach
Auditing Through the Computer – Using CAAT’s
Auditors are now increasingly adopting the latter approach for better meeting of ends.
Manual Information systems allowed auditors to apply procedures through personnel interactions, general observations, by assessing the capabilities of staff in understanding & discharging their roles effectively and in other like ways.
Increased usage of Hybrid and Fully Automated Information systems emphasis the need of the hour for auditors to equip new skills in the following broad areas:
- Understanding Computer Concepts & System design
- Understanding Accounting Information systems (AIS) and how Internal Controls are mapped on to computers to manage technology & business risks.
- Knowledge of use of computers in Audit. (IT Audit Specialists)
Now a days, It is not uncommon for auditors to get replies (from auditees) like:
“The system takes care of Everything. We cannot intervene at all !!”
“We can only provide Reports as generated by our systems. Customization as per your requirements is not possible !”
“Robust controls are in place. The computer itself dictates our roles.”
“No one but the computer only knows the entire flow of work”.
Then, in the absence of any specific knowledge of systems,
How do the auditors gain the understanding of an Entity in Automation Environment?
How do they assess the sources of information for evidence?
Who to cross check with, the authenticity of Transaction Processing?
Where to go for an Audit Trail & Documentation?
Most importantly, What ensures the existence of Consensus Ed Idem among the systems, people and procedures to see that the entity is progressing towards the desired goals?
The following section makes an attempt to answer the above questions.
Implementing IT Related Aspects of Risk Based Auditing
Information technology (IT) requires special consideration in the practical application of risk-based auditing, as defined under both the AICPA Risk based Audit standards -Statements on Auditing Standards (SAS) 104–111, and the Public Company Accounting Board (PCAOB) Auditing Standard (AS) 5.
Both SAS 104–111 and AS5 emphasize the need to establish tight linkage between audit procedures and a thorough assessment of financial statement and assertion level risk. Both standards reference the role of IT as a potentially significant source of inherent audit risk.
The risk-based audit standards adopted by the AICPA in 2006, along with AS5 released in 2007, emphasize a top-down, risk-based approach to the financial audit.
The Overall approach for IT considerations in Risk based auditing is as follows:
A) Planning Risk Assessment Procedures : IT Specialists
An Audit Plan must define how the auditor will gain understanding of the role of IT for Material Transactions, Financial Reporting and Material Disclosures. The common objectives like identification of Inherent, Control & Detection risks, effectiveness and adequacy of IT controls, FAP’s etc, remain the same.
However, depending on the complexity of IT systems, a IT audit professional will need to be part of the audit team. He must be able to perform general auditing, understand flow of financial data, effect of system based functions on accounting results, designing & performing Tests of IT controls and Substantive procedures using Computer Assisted Audit Techniques (CAAT’s).
B) Understanding the IT Environment & Related Controls
The role of IT in initiation, authorization and recording, processing & reporting should be gathered from the entity’s information systems, which may include Packaged Applications, Custom Developed applications & end user computation items like spreadsheets that are used for Transaction cycles like revenue recognitions and containing accounting balances.
IT controls may be broken down as follows:
1) Application Controls: These relate to the transactions & standing data in a computerized accounting system. They are specific to a given application and ensure the completeness and accuracy of Accounting records & also the validity of the entries made therein. They shall be observed and confirmed as part of normal walk through procedures.
The following are its components:
(I) Input Controls – Designed to ensure that input is authorized, complete, accurate and timely. They consider cost benefit analysis, confidentiality requirements of data. On screen prompt facilities (eg : requesting users for bio metrics) and facility for audit trail to trace a transaction from origin till disposition are common examples. Specific Input validations may include:
- Format Checks (eg : dates to be numerical only)
- Range Checks (eg: bulk purchases exceeding certain amt. to be referred for follow up)
- Compatibility Checks (eg: sales invoice amt. to be in line with sales tax charged)
- Validity Checks (eg: cost input for already completed jobs to be rejected)
- Exception Checks ( eg: generation of exception reports while any Negative inventory is purported to be carried forward)
- Sequence Checks (eg: documents processed out of sequence while receiving pre numbered goods into physical inventory are rejected)
- Control Totals (eg: non matching totals of a batch of purchases with pre input data should result in follow up report)
- Check Digit Verification – Using Algorithms to ensure data input accuracy (eg: rejection of indents with invalid reference to internally generated listed suppliers reference codes.)
(II) Processing Controls – Ensures that all data inputted is processed accurately and the data files are updated timely. These must be tested prior to live running with real data. They also ensure the integrity of the data from one processing run to other. Subsequent processing of rejected inputs are taken care of as well.
(III) Output Controls – They ensure that all data is processed and to authorized persons only.
(IV) Master File Controls – They ensure the ongoing integrity of the standing data. Meticulous security controls have to be exercised over all master files. Regular scrutiny of master data to authorized data is a common procedure to ensure integrity.
2) General Controls: They function to protect the integrity of an entity’s applications as a whole. Data & Programs are protected from unauthorized changes. Assurance regarding availability & reliability of computer systems can be taken from these controls, especially where auditors have to rely on accounting data from multiple applications. Auditors to ensure adequacy & operating effectiveness for procuring reliable audit evidence.
Change Management, Security management, Back up & recovery, Operations control & access controls are the processes involved.
Its components are as follows:
(I) Admin Controls – They take care of Data Center, Network Operation and Access Security to,
- Prevent/Detect errors in program execution (eg: manuals preparation, training of staff, using obsolete versions etc)
- Prevent unauthorized amendments to data files
- Ensure continuity of operations
(II) System Development Controls- They look after the areas of system & application software acquisition, development & maintenance which include:
- Controls over program development like prescribing Good Standards for code writing, documentation, testing & segregation of duties.
- Controls over program changes.
- Controls over installation & maintenance.
Such an elaborate discussion of IT controls is done to clarify the broad framework within which various entities implement their own Computerized Information systems. As each organization would have ERP’s & software tailor made to suit its requirements, it would be impracticable to emphasize any single program. Instead, an attempt was made to review the functionalities, usages and modus operand of the widest possible controls. This would enable the auditors to judge whether the customized IT systems possess all these bench mark qualities in an effective & adequate manner.
(C) Computer Assisted Audit Techniques & Risk Assessment:
The auditors may choose to use the Auditees CIS itself or employ their own computers as audit tools. The extent to which an auditor uses CAAT’s & manual techniques would depend on following factors:
- Practicality of Manual Testing, given to volume of data
- Cost effectiveness of CAAT’s
- Availability of audit time & client’s computers facility
- Level of Experience & Expertise in using CAAT’s
- Extent to which CAAT’s are used in Internal Audit functions & how external auditor relies on the same.
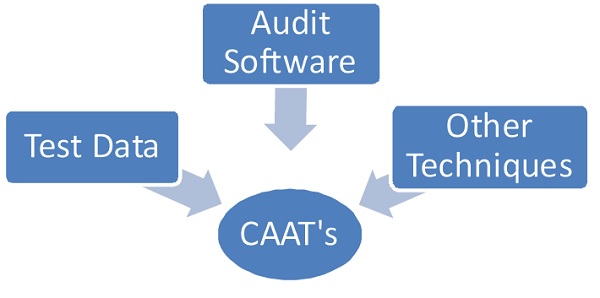
1) Audit Software : These are the programs designed to carry out Test of controls & Substantive procedures, which include
- Packaged Programs – These are pre-prepared generalized programs that are not client specific, used for selection of statistical samples, arithmetical calculations and for checking gaps in processing sequences.
Most popular examples are Audit Control Language (ACL) & Interactive Data Extraction and Analysis (IDEA).
- Purpose Written Programs – These are client specific. They may be bought / developed but the audit plan must ensure the program appropriateness to a client’s system. They are very useful in Re-performing computerized control procedures of clients (eg: re-computation of cost of sales, aging analysis of receivables etc). They are used for establishing Audit Trail.
- Enquiry Programs – They are integral to the client’s accounting system which may be adapted for audit purposes. These include monthly based reports of employees salaries, long outstanding creditors balances etc.
2) Test Data :
- Audit Test Data – It is used to test the Existence & Effectiveness of controls built into application programs. Certain Dummy transactions are processed through client’s computerized system, the results of which are then compared with the auditors expected results. This is done to ensure the system’s Objectiveness & Integrity.
For example, 2 dummy cash / purchase transactions are entered by the auditor, wherein one falls within the system parameters and the other disobeys the same. If the expected output of error report is not generated, the auditor will have to go for substantive procedures for the review area.
- Integrated Test Facilities – In the audit test data, sometimes there is a risk of corrupting the auditees live data by processing it with test data. To avoid such mishaps, the auditor may establish an integrated test facility within AIS of client itself, which requires establishment of a dummy unit , say, a dummy creditors / distributors account , against which the test data is processed during the normal processing runs itself.
The major disadvantage is auditors do not have total assurance that test data is processed similar lines as live data.
3) Other Techniques :
- Embedded Audit Facilities (EAF’s) – In this technique, auditor’s own code in incorporated into client’s software, so that verification can be carried out as required on the data processed.
For example, the tests of controls may be carried out by tagging certain transactions which are then followed through the systems to ascertain whether all the controls & procedures have been applied or not.
EAF’s should ensure that the results are saved in master secure files for subsequent review by auditor to conclude on system integrity.
EAF’s also enable simultaneous application of Analytical Review Programs.
- Application Program Examination – Where system amendments have occurred during an accounting period, auditor needs assurance that necessary controls existed both before & after amendments. This is achieved by comparing the controls prior to & after the amendment date.
This is necessary in determining the extent to which auditors can rely on the application controls.
The above is not an exhaustive list of CAAT’s. The auditors are entailed to tap their professional experience, skepticism & entity’s knowledge for evolving innovative methods to counter various client specific audit situations in assessing the significance & relevance of risks.
(D) Designing & Performing Further Audit Procedures
Having tested the controls & transaction processing in AIS, the auditor can very well now give his response to the Significant Risks with audit procedures which are equally strong & complex as the risks calling for increased attention.
The Audit program, at this stage needs to be proactive according to the Nature, Timing and Extent of Procedures performed. Care must be exercised in determining the relevance of audit evidence and sampling guidance while amending the audit plan.
Once, the specific procedures are ascertained, they would performed and results added to Audit Working Papers
(E) Evaluation of Audit Evidence, Findings, Control Deficiencies & Final Audit Report
The Audit team should discuss audit findings at phases of risk assessment, audit planning, further audit procedures, together with the evidence gathered at each such phase and also evaluate control deficiencies.
At this juncture, the final Risk Based Audit Report should not only focus on mitigating the Audit Risk to an acceptably low level, but also to communicate the significant findings to Management & Those Charged with governance to counter the pervasive effects of such risks in future.
Below is a Summary Flowchart for the Risk Based Auditing in IT Environment 
Conclusion:
This entire exercise of brainstorming with computers reminds me a famous maxim,
“Survival of Those Most Adaptive to Change”
Now, the time has come for adjusting our course towards Digital Audits & Paperless procedures. We are not alone in this battle, scores of software’s and tools are available in the market for assisting us. A glance would reveal the following popular one’s:
- GRC Cloud for Risk Assessment, Internal controls
- Optial Smart Start Business Review & Check list based audits
- Compliance Bridge for Automated systems of Publishing & Monitoring Audit plan compliance.
It is a Great Opportunity for the Auditors Fraternity to re-establish the capability of our profession in standing the Tests of Time in conducting ever Adaptable Audits.




